What’s the Deal With Secure Connections?
Why Is It Important?
When browsing the internet or making other connections these days, everyone wants to make sure that the communication taking place is secure and encrypted. Plex has teamed up with Let’s Encrypt to provide our users with high-quality secure certificates for your media servers, at no cost to you. There’s no need to set up VPNs and no need to create and install your own certs. You can safely and securely connect to your media no matter where you are.
After all, everyone loves to see beautiful secure locks, right?
Our blog post announcing the release of secure communications spoke about some of the details:
Let’s look at some of the complexities: For starters, secure communication requires something called a certificate, which securely identifies a website. Now anyone can make a (self-signed) certificate, but it can be tedious to install, and for a browser to trust it and give it that elusive green lock, it has to have been signed by a trusted authority. It’s a pretty laughable security experience if the browser warns you that your server isn’t trusted! We knew from the start that we needed real, official certificates, and there are a few problems with that. For starters, they’re expensive, especially when multiplied by a bazillion. And we knew we wanted to give a secure experience to everyone, not just our Plex Pass users. And that’s why we hooked up with the amazing team at DigiCert, and they were all “you want an ungodly amount of certs? We can do that!” So yeah, we’re buying you all DigiCert certificates for your media servers. Because we love you.
Secondly, as mentioned before, we’re on a lot of platforms, and there are lots of nuances to secure communication. For example, did you know that Internet Explorer requires Diffie-Hellman parameters to be larger than 512 bits? Did you know that certain models of LG TVs ship with a specific set of root certificates which is missing some common ones you might expect? Frankly, I hope you have no clue what I’m talking about here, because it gave us some major headaches along the way.
Next is the server itself, which doesn’t just have to support HTTPS, it has to do so avoiding many pitfalls, crocodiles, and whatever else was in that awesome game. Thankfully there are tools to help with that, and they even give you a grade. Let’s just say the Plex Media Server is an overachiever! Its parents are so proud.
Last of all, the media server can be accessed both remotely and on a LAN. At any given time, it may be accessible via multiple addresses. Certificates are generally associated with a small set of unchanging IP addresses. So we’ve worked some DNS magic to remove that limitation, and make things Just Work.
The end result is that you get that beautiful lock and a secure connection! (Note that while certificates were originally provided by “Digicert”, which is referenced in the quote, certificates are currently provided by “Let’s Encrypt”.)
If you’re interested in some of the more technical details, Filippo Valsorda did an excellent writeup after the initial release.
Related Page: Filippo Valsorda: How Plex is doing HTTPS for all its users
Are All the Communications Secured?
When you’re using a Plex app that supports secure connections (see below) to connect with a secure Plex Media Server, the requests to and communication with that Server are secure. If you stream media from the server, that streaming is also secured. There are a few, very specific circumstances in which communication won’t be secure:
- Flinging/casting content using our Plex Companion protocol will not always be secure.
- When making use of a “Manual Connection” that you’ve explicitly and manually added in particular Plex apps (e.g. Android or Roku), the communication won’t be secure.
- Internal, local requests from the System and Framework components to the rest of the Plex Media Server are over regular HTTP. These requests are only within the local machine itself.
Editing Secure Connections Setting
By default the Secure Connections setting on your Plex Media Server is set to Preferred. That means that secure connections will always be used when one is available (a non-secure connection will only be used when a secure one isn’t possible/available). So. there isn’t even anything special you need to do unless you want to require secure connections at all times (meaning that connections will simply fail if it’s not possible to connect securely).
- Sign in to your Plex account in the server.
- Go to Settings > Server > Network in the Plex Web App (and toggle the Advanced settings to be visible).
- The Secure connections setting can be adjusted there.
Related Page: Sign in to Your Plex Account
Related Page: Network
Which Apps Support Secure Connections?
The following Plex apps support secure connections to your Plex Media Server:
- Amazon Fire TV
- Android (mobile)
- Android TV
- Apple TV
- Chromecast
- iOS
- macOS (desktop)
- PlayStation
- Plex HTPC
- Plex Web App
- Roku
- Smart TVs
- LG (4K/UHD [webOS 3.0+])
- Samsung (4K/UHD 2016+ models)
- VIZIO SmartCast
- Sonos
- Windows (desktop)
- Xbox
Related Page: Plex Downloads page
How Do I Know Connections Are Secure?
Basically, in a default Plex setup, if you don’t see any information indicating otherwise, then the connection to the server is secure. When a secure connection to a server is not available, the app will typically indicate either that the connection is insecure or that a connection cannot be made (because it would be insecure and that isn’t allowed in the app).
Plex Web App
Hosted Web App
When you go visit our hosted web app at app.plex.tv in a browser, the app will automatically load securely.
- If your account is associated only with secure servers, you’ll connect securely to https://app.plex.tv/desktop
- If any of your associated servers don’t support secure connections, those insecure servers will not be accessible in the app. You can instead try loading the local/bundled web app that comes with the server install.
So, if you have all secure servers, you’ll always be connected securely!
Tip!: You can always manually go to https://app.plex.tv/desktop to force using a secure connection to Plex Web App. Of course, if your servers don’t support secure connections, then they won’t be accessible.
Using the Bundled Plex Web App
By default, the local, bundled version of Plex Web App will load over HTTP. While the app itself may have loaded insecurely, it can still make secure connections to individual servers that support secure connections. That said, we still generally recommend using our hosted web app (app.plex.tv), even on your local network, since it can still stream locally and it ensures you’re running the newest web app version.
You can, of course, attempt to force an HTTPS connection simply by using https:// in the URL. If you do so, since the server’s certificate isn’t for “localhost” (for example), your browser will almost certainly warn you that there isn’t a valid certificate for that connection.
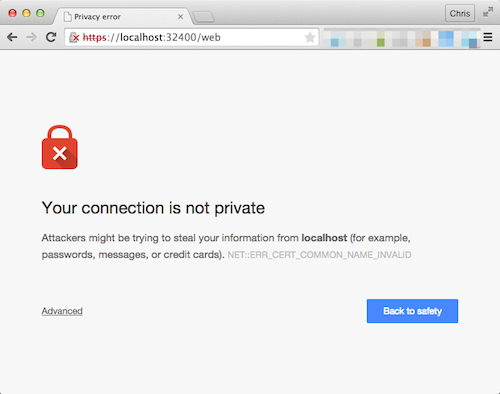
You can make an exception there if you wish, but you won’t see the lock in the address bar as you would if using the standard hosted web app securely. If you wish to see the lock in the address bar, you’ll want to connect as described earlier.
What About Connecting By IP or Custom Access URL?
Some users may be used to accessing their server’s bundled Plex Web App through something like http://public.wan.ip.address:32400/web or http://mycustomredirecteddomain.com:32400/web when away from home. If you just switch to using https:// in the URL, you’re going to see the same sort of behavior as described above for ‘Using the Bundled Plex Web App”. The certificate that’s been issued to your server isn’t signed for your IP address or your custom domain, so it won’t report itself as valid for those.
Instead, simply launch the hosted web app app (app.plex.tv) as described previously, so that you can take advantage of the secure connections as intended.
Why Isn’t It Working? (DNS Rebinding)
In rare cases, your apps still may not be able to connect securely with your Plex Media Server. In nearly all cases, this will be caused by issues with your router/modem or network.
Some routers or modems have a feature known as “DNS rebinding protection”, some implementations of which can prevent an app from being able to connect to a Plex Media Server securely on the local network. For most users, this won’t be an issue, but some users of higher-end routers (or those provided by some ISPs) may run into problems.
Similarly, some DNS providers (including some ISPs) may have this feature.
DNS rebinding protection is meant as a security feature, to protect insecurely-designed devices on the local network against attacks. It provides no benefit for devices that are designed and configured correctly.
ISP Settings
In some cases, your ISP itself may provide rebinding protection when using their DNS services. In this case, you can switch to using a different DNS service. Depending on your personal setup, you may need to update either your router’s configuration, the configuration on your computer(s), or both.
There are many free, easy-to-use, quality alternative DNS services. Some of the more popular:
- https://1.1.1.1/ (a “privacy-first” DNS responder)
- Quad9
- Google Public DNS
- OpenDNS
Modem/Router Settings
We can’t provide instructions for all possible configurations, but the most common scenarios for this issue include using “dnsmasq” (often on DD-WRT based routers), and using pfSense. You may need to consult your router’s documentation for more details about DNS rebinding protection.
dnsmasq
To allow secure connections to work correctly on the local network if you are using “dnsmasq” with DNS rebinding protection enabled, you will need to add the following line to your configuration file (the “advanced settings” box in DD-WRT):
rebind-domain-ok=/plex.direct/Related Page: Manpage for Dnsmasq
pfSense DNS Resolver
Similarly, if you are using pfSense’s internal DNS resolver service (specifically the “ISC DNS” resolver), you’ll want to adjust that configuration. In the pfSense web UI, go to Services > DNS Resolver, click Display Custom Options, and enter the following the the text box:
server:
private-domain: "plex.direct"Related Page: pfSense: DNS Rebinding Protections
Remote Access Workaround
In some cases, it may be possible to work around DNS rebinding protection by enabling Remote Access for your server. When enabled, this allows connections to be made via your public/WAN address. In most cases, your router will automatically keep such connections within your LAN, though this isn’t universal across all routers.
Warning: When working around DNS rebinding protection this way, your apps and Plex Media Server will typically treat the connections as being from a “Remote” source. This can affect which streaming qualities are used, as well as trigger Remote-applicable server bandwidth and transcoding limitations.
Related Page:
Related Page: Troubleshooting Remote Access
